Cyber 2.0 prevents the spread of cyber-attacks in two different networks
Cyber 2.0 prevents the spread of cyber-attacks that every other defense system in the organization failed to stop (NDR)
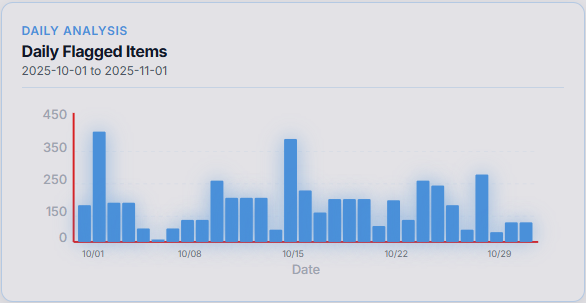
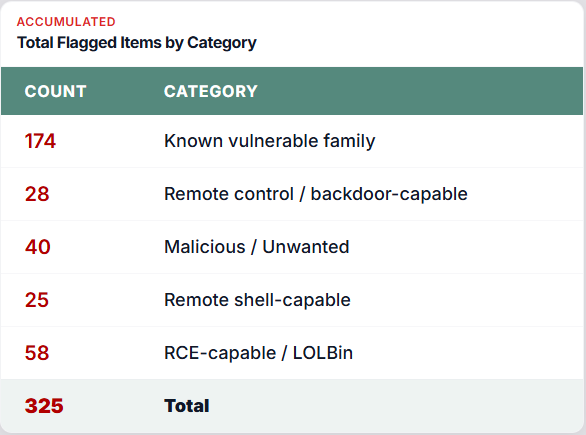
Every customer receives a report with the list of malware that successfully bypassed all other cybersecurity systems, and was blocked by Cyber 2.0
Cyber 2.0 is the only solution that delivers true prevention, ensuring that only authorized computers running authorized software can access industrial controllers
Cyber 2.0 Vs All Other Systems
We expose others’ ultimate weaknesses by demonstrating their failure to prevent attacks
All cyber systems are installed on every computer, including the infected one
Cyber 2.0 blocks every malware after it had bypassed all other systems

The Proof
Providing each client with an AI-based report
The report includes a list of all malicious software, and vulnerable software exploited by attackers that bypassed all other cyber defenses systems, successfully exited an infected computer and attempted to spread within the organization
Cyber 2.0 stopped them, before they could even enter the targeted computers
The full list is attached in Excel sheet that includes Details about each software:
- The source — from which computer
- The time — when it was sent
-
The destination — where it attempted to reach
Each customer can easily verify that these malicious did, in fact, penetrate all their other defense systems
Our Technology
Other cybersecurity companies
Attempt to prevent malware from:
1. Entering to one of the computers (firewalls)
2. Infecting המחשב exiting from it to the network (EDRs)
Cyber 2.0 solution
Cyber 2.0 (NDR) takes the opposite approach
1. It allows malicious programs to exit without interference
Cyber 2.0’s Blocking
Cyber 2.0 blocks their entry into the rest of the computers
PARADOXICALLY
Allowing exit from an infected computer ensures blocking on the receiving side
BY DEFINITION
Every attack blocked by Cyber 2.0 on the computer it was targeting is an attack that exits from another infected computer, after having already bypassed all cyber defense systems.
The Analogy
The Goalkeeper Principle
- Every ball stopped by the goalkeeper is one the defenders failed to stop
- Every football team can afford to lose a defender or two but it can’t afford to lose its goalkeeper
- Every organization can manage without some of its cyber defenses but it can’t afford to be without Cyber 2.0

We Solve Two Fundamental Cybersecurity Problems
PROBLEM
Detection
No cyber company can identify every new attack (Zero-Day)
Using AI creates thousands of mutations — impossible to detect all
SOLUTION
Zero Trust
WHAT WE DO
System does not need to detect each new attack
HOW WE DO IT
1. Define which software is allowed to move
2. All others = unauthorized
PROBLEM
Prevention

Defense systems can’t block programs they failed to identify
Hackers attack → Neutralize defenses → Malware spreads
SOLUTION
TrustMathematical Chaos
WHAT WE DO
Continues protecting even if attackers removed it
HOW WE DO IT
1. Not allowed software exits freely
2. Blocking done on receiving computers
3. homepage.problemsSolutions.solution2How3
The Chaos Model
Other Cyber Companies
Based on
Biological Models
Therefore vulnerable to attacks by hackers using similar models
(Hence all the terminology: virus, antivirus, mutations, etc.)
Cyber 2.0
Based on
Mathematical Chaos Theory
Which is unbreakable
(Even we can’t crack it)
The company has registered 9 patents for the system
video
Additional Advantages

Cost
The Cyber 2.0 system doesn’t add costs to the organization
On the contrary, it reduces costs, as it can replace multiple other

Virtual NAC
Enables only authorized devices to connect, inside or outside
the organizational network with no new hardware and zero IT hassle

No Overload
Operates without slowing down the network

Regulation
Operates without reading personal or private data.
We are not only compliant with GDPR – we assist organizations in meeting regulations

Updates
No software updates are required

Remote Work
An infected home computer will not infect the organization
